Just recently a research group called Rapid7 published a report that reveals over a year’s worth of research regarding malicious activity tethered to Bitcoin Core (BTC) full nodes. By utilizing data collected from a network called ‘Project Heisenberg,’ and its internet scanner ‘Project Sonar,’ alongside intelligence from Bitnodes, the team had found quite a lot of exploits being shared between full blockchain nodes.
Also read: The Hitchhikers Guide To The Invisible Internet
Study Finds Bad Actors Throughout Bitcoin Network’s Public Nodes
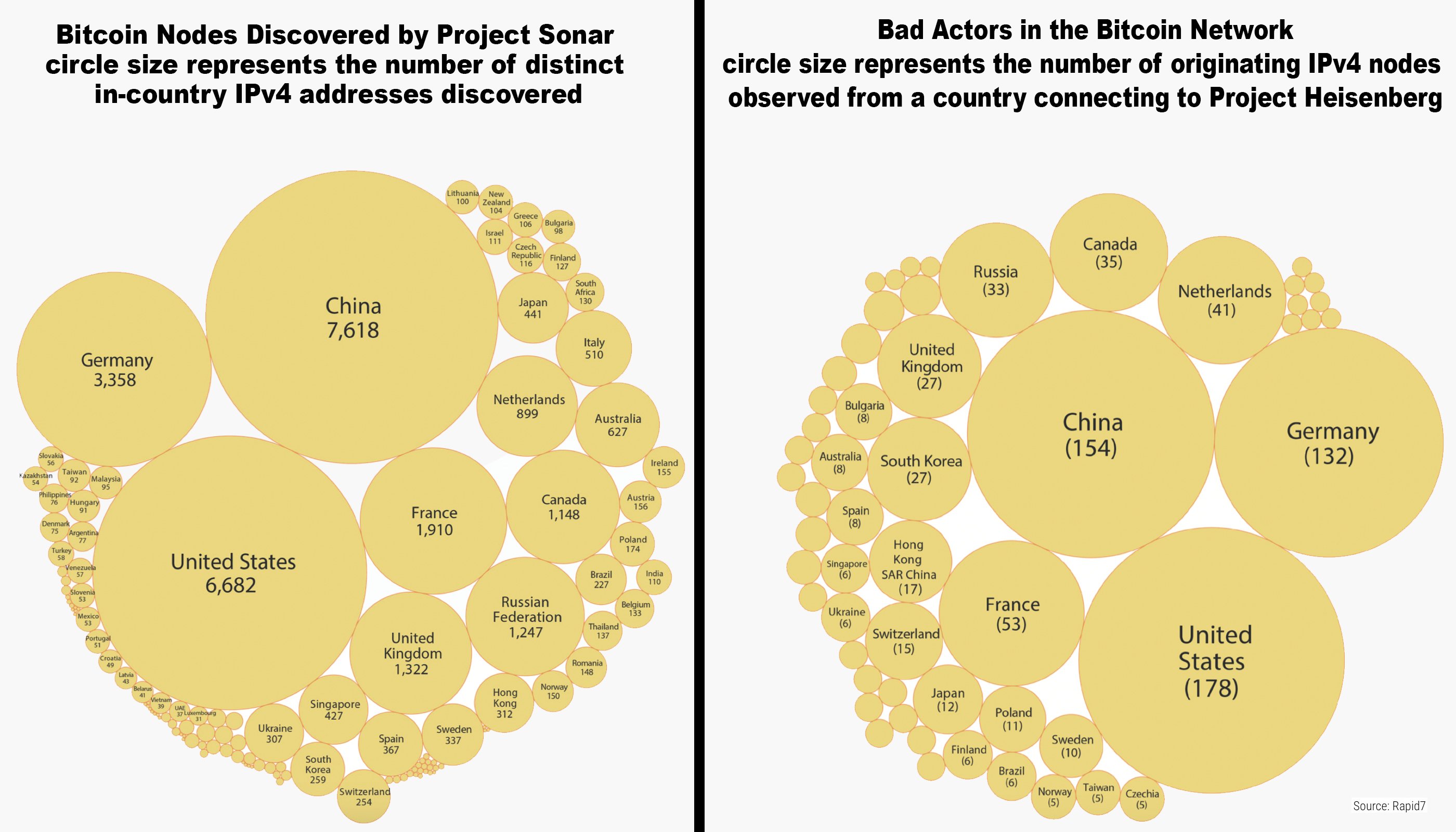
Bitcoin full node operators connect usually connect by default to a TCP service on port 8,333, but there are also over 600 alternative ports available. Rapid7’s recent research used data from the team’s Project Sonar which revealed the top three countries with the most port 8,333 nodes stem from the U.S., China, and Germany. The researchers began the blockchain surveillance back in August of 2017 and found more than 11,000 nodes per day. Moreover, the researchers collected data from more than 144,000 unique full nodes during the course of the study.
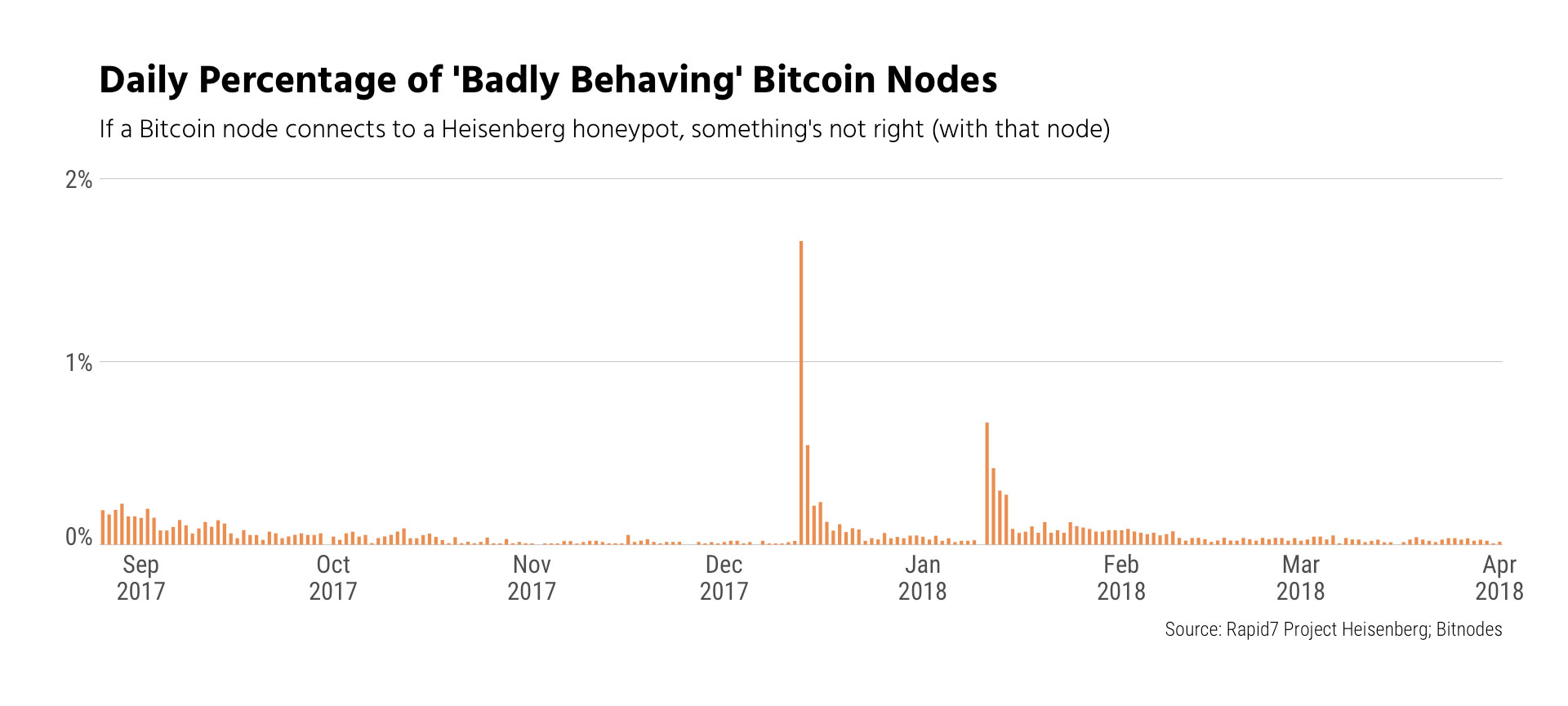
In addition to the Project Sonar intelligence over 900 nodes connected to Rapid7’s honeypot technology Project Heisenberg that revealed interesting and some malicious activities like the distribution of MS17-010 a critical Microsoft operating system vulnerability.
“Investigations into these interactions showed familiar patterns. Port scans and active reconnaissance with tools like Nmap were rampant, as was repeated attempted exploitation of MS17-010, largely from China,” explains Jon Hart a Rapid7 researcher.
17 hosts, mostly from the China IPv4 space, were actively slinging exploits for MS17-010.
The Bitcoin Network Three Times More Evil Than the Public Internet
As mentioned above most of the shady activities derived from confirmed malicious nodes with the